Windows Event Id 1
Apr 19, 2017 Restricted Admin Mode Version 2 Type = UnicodeString: Only populated for RemoteInteractive logon type sessions. Chinese sks serial numbers lookup. This is a Yes/No flag indicating if the credentials provided were passed using Restricted Admin mode. Restricted Admin mode was added in Win8.1/2012R2 but this flag was added to the event in Win10. Sysmon Event ID 1. Source: Sysmon: Discussions on Event ID 1 Ask a question about this event. 1: Process creation. Free Tool for Windows Event Collection. Discussions on Event ID 1. Ask a question about this event Upcoming Webinars Anatomy of an Attack: MitM into O365, defeat MFA, then Lateral Movement into On-Prem. Apr 26, 2018 Describes an issue in a Hyper-V guest operating system of Windows Server 2008 R2 or of Windows 7 in which the VDS Basic Provider event ID 1 is logged. Windows Event Log Analysis Splunk App Build a great reporting interface using Splunk, one of the leaders in the Security Information and Event Management (SIEM) field, linking the collected Windows events to www.eventid.net.
Monitor unlimited number of servers
Filter log events
Create email and web-based reports
Direct access to Microsoft articles
Customized keywords for major search engines
Access to premium content
Windows Event Log Id List
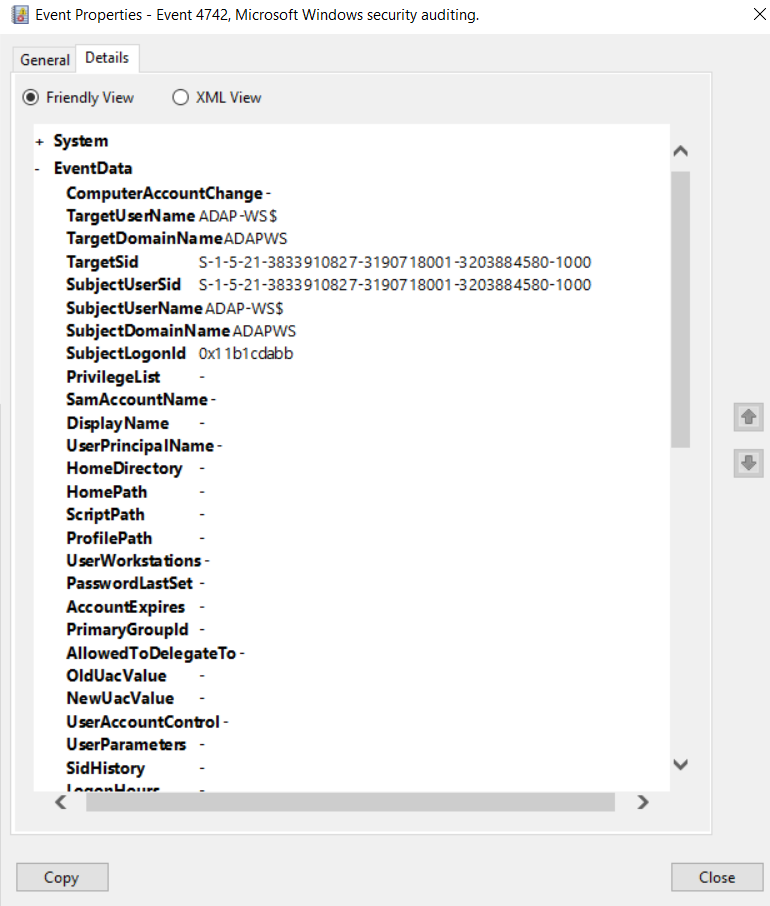

Windows Event Id 1001
Microsoft Event Id List
'<error description>'
Happened while starting this command:
<command>
Evy, the EvLog Artificial Intelligence module, detects anomalies, inconsistencies, unusual patterns and changes adding knowledge and reasoning to existing environments.
When enabled, Evy starts collecting statistics about events recorded on your computer. As it's the case with any intelligent entity, Evy will get smarter as EvLog evolves and more sets of data are analyzed.
In time, Evy will be able to detect patterns in the logs, diagnose problems, and do some of the thinking assisting the overworked system admins of the world!
Build a great reporting interface using Splunk, one of the leaders in the Security Information and Event Management (SIEM) field, linking the collected Windows events to www.eventid.net.
Windows Event Id 153
Obtain enhanced visibility into Cisco ASA firewall logs using the free Firegen for Cisco ASA Splunk App. Take advantage of dashboards built to optimize the threat analysis process.



